CrowdInspect 1.5.0.0
CrowdInspect is a powerful tool designed to help businesses protect their network from malicious malware. With its advanced capabilities, it is able to identify suspicious network activity in real-time, providing added security to your system.Enhancing Cybersecurity with CrowdInspect
Understanding the Importance of Detecting Malware Communication over the Network
It is crucial to understand the importance of detecting malware communication over the network. Malware, a malicious software designed to infiltrate and compromise computer systems, poses a significant risk to individuals and organizations alike.
One powerful tool that aids in this detection process is CrowdInspect. This innovative software solution plays a vital role in network security by identifying and analyzing suspicious network traffic patterns associated with malware communication. By monitoring network traffic in real-time, CrowdInspect helps cybersecurity professionals identify potential threats before they can cause substantial damage.
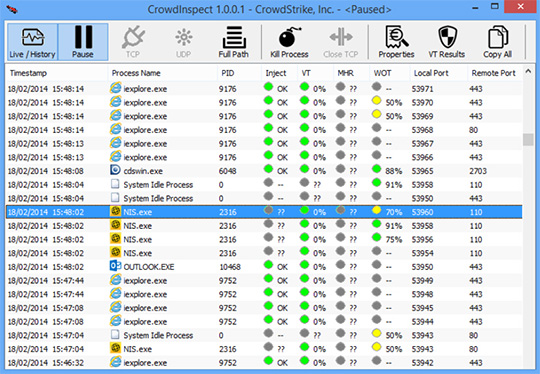
CrowdInspect provides detailed information about each process, such as its file path and digital signature, enabling users to make informed decisions about whether to terminate or quarantine the process.
The Role of CrowdInspect in Analyzing Network Traffic and Identifying Suspicious Behavior
CrowdInspect offers a range of powerful features that enable organizations to effectively monitor and analyze network traffic. By leveraging its cutting-edge technology, CrowdInspect can detect and flag potential threats in real-time, helping businesses stay one step ahead of cybercriminals.
One of the key strengths of CrowdInspect lies in its ability to identify malware indicators within network traffic. With its sophisticated algorithms and deep packet inspection capabilities, it can swiftly detect malicious activities that may go unnoticed by traditional security measures.
CrowdInspect goes beyond mere detection by providing detailed insights into suspicious behavior patterns. It carefully analyzes network traffic data to uncover anomalies and unusual activities that could indicate a potential breach or compromise.
CrowdInspect proves to be an invaluable asset in the fight against cyber threats. Embracing this powerful tool empowers organizations with enhanced visibility into their networks' security posture while enabling them to take proactive measures to protect sensitive data from malicious actors.
1. Real-time Monitoring and Alert System
CrowdInspect provides a comprehensive solution for proactive threat detection. With its cutting-edge capabilities, it continuously monitors network traffic, system logs, and user behavior to identify any suspicious activities or potential security breaches.
One of the key advantages of CrowdInspect is its ability to provide instant alerts. As soon as a potential threat is detected, the system triggers an immediate notification to the relevant stakeholders. This enables organizations to take swift action and mitigate risks before they escalate into major security incidents.
The real-time nature of CrowdInspect's monitoring ensures that no potential threat goes unnoticed or unaddressed. By constantly analyzing data patterns and correlating information from multiple sources, it offers unparalleled visibility into the organization's security posture.
Moreover, CrowdInspect goes beyond traditional security measures by incorporating machine learning algorithms that adapt and evolve over time. This means that it can detect even the most sophisticated threats that may attempt to bypass conventional defense mechanisms.
2. Identifying Command-and-Control (C2) Servers
CrowdInspect helps security professionals identify and track down these malicious servers. It provides real-time monitoring and analysis of network traffic, allowing for quick identification of suspicious communication patterns.
Additionally, IP reputation checks play a significant role in identifying C2 servers. By analyzing the historical behavior and reputation of an IP address, security analysts can determine if it has been associated with malicious activities in the past. This information helps prioritize investigations and take appropriate actions to mitigate potential threats.
Furthermore, domain analysis is another important aspect when it comes to identifying C2 servers. Analyzing domains associated with suspicious IPs or URLs can provide valuable insights into their intentions and connections to known threat actors or campaigns. By examining factors such as domain registration details, SSL certificates, and hosting infrastructure, security professionals can uncover hidden links between malicious entities.
3. Analyzing Network Connections for Anomalous Behavior
CrowdInspect specializes in anomaly detection in network connections, allowing organizations to identify and investigate any unusual communication patterns or protocols.
By leveraging advanced algorithms and machine learning capabilities, CrowdInspect can analyze vast amounts of network data in real-time. It can detect deviations from normal behavior, flagging any suspicious activities that may indicate a potential security breach or unauthorized access attempt.
Detecting anomalous behavior in network connections is crucial for early threat detection and response. By identifying unusual communication patterns or protocols, organizations can take proactive measures to mitigate risks and safeguard their sensitive data.
The Benefits of Using CrowdInspect for Malware Detection and Mitigation
CrowdInspect offers advanced features that enable proactive defense against malware attacks. By leveraging the power of crowd-sourced intelligence, it provides real-time insights into potential threats and helps organizations stay one step ahead of cybercriminals.
One of the key benefits of using CrowdInspect is its ability to detect and identify malicious software quickly and accurately. Its advanced scanning capabilities analyze files, processes, and network connections to identify any suspicious behavior or indicators of compromise. This allows organizations to take immediate action to mitigate the risks associated with malware infections.
CrowdInspect's crowd-sourced intelligence ensures that its threat database is constantly updated with the latest information on emerging threats. This means that users can benefit from collective knowledge and experience in detecting new types of malware, enhancing their overall defense strategy. Utilizing CrowdInspect for malware detection can enhance their cybersecurity defenses and protect their valuable data from malicious actors.
How to Effectively Use CrowdInspect to Detect Malware Communication over the Network
It is crucial to ensure that you have the latest version of CrowdInspect installed on your system. Regularly updating the software will provide access to the most up-to-date threat intelligence and detection capabilities, enabling you to stay ahead of emerging malware threats.
Next, familiarize yourself with the various features and functionalities offered by CrowdInspect. Take the time to explore its interface, understand how to navigate through different sections, and learn about its different scanning options. This will enable you to make full use of its capabilities and tailor its settings according to your specific needs.
When using CrowdInspect, it is recommended to run scans during periods of low network activity. This will minimize potential interference or false positives caused by legitimate network traffic. Additionally, consider scheduling regular scans at predetermined intervals or during off-peak hours for comprehensive coverage without disrupting critical operations.
To optimize accuracy, ensure that all relevant devices are connected to the network when conducting scans with CrowdInspect. This includes servers, workstations, laptops, mobile devices - essentially any device that may be vulnerable to malware communication. By scanning all connected devices simultaneously, you can obtain a comprehensive overview of potential threats across your entire network infrastructure.
Take advantage of any customization options available within CrowdInspect. Tailor scan settings based on your organization's specific requirements or industry standards. Adjusting parameters such as scan depth or sensitivity levels can help fine-tune detection capabilities and reduce false positives.
Regularly review scan reports generated by CrowdInspect for any suspicious activity or indicators of compromise (IOCs). Pay close attention to any anomalies detected during scans and promptly investigate them further if necessary. This proactive approach will enable you to swiftly identify and mitigate potential threats before they can cause significant harm to your network.
Strengthen Your Security Strategy with CrowdInspect's Powerful Capabilities
If you want to strengthen your security strategy and elevate your cybersecurity posture, CrowdInspect is the solution for you. With its powerful capabilities, CrowdInspect can effectively detect and mitigate malware communication, providing you with the peace of mind that your systems are protected.
By leveraging the advanced features of CrowdInspect, you can stay one step ahead of cyber threats and ensure the integrity of your network. Its ability to analyze network traffic and identify suspicious behavior allows you to proactively respond to potential attacks before they cause any damage.
CrowdInspect offers a comprehensive solution that not only detects malware communication but also provides insights into potential vulnerabilities in your network infrastructure.
Don't leave your organization's security to chance. Strengthen your security strategy today by incorporating CrowdInspect's powerful capabilities into your cybersecurity framework. Safeguard your sensitive data and protect against malicious activities with this cutting-edge tool. Trust in CrowdInspect to provide you with the protection and peace of mind you need in today's digital landscape.
Conclusion
To conclude CrowdInspect works on Windows operating system(s) and can be easily downloaded using the below download link according to Freeware license. CrowdInspect download file is only 530 KB in size.CrowdInspect was filed under the Adware, Spyware and Virus Protection category and was reviewed in softlookup.com and receive 5/5 Score.
CrowdInspect has been tested by our team against viruses, spyware, adware, trojan, backdoors and was found to be 100% clean. We will recheck CrowdInspect when updated to assure that it remains clean.
CrowdInspect user Review
Please review CrowdInspect application and submit your comments below. We will collect all comments in an effort to determine whether the CrowdInspect software is reliable, perform as expected and deliver the promised features and functionalities.Popularity 10/10 - Downloads - 88 - Score - 5/5
Softlookup.com 2023 - Privacy Policy
| Category: | Adware, Spyware and Virus Protection |
| Publisher: | CrowdStrike |
| Last Updated: | 06/12/2023 |
| Requirements: | Windows 10 64-bit / Windows 10 / Windows 8 64-bit / Windows 8 / Windows 7 64-bit / Windows 7 |
| License: | Freeware |
| Operating system: | Windows |
| Hits: | 533 |
| File size: | 530 KB |
| Price: | Not specified |
| Name: * |
E-Mail: * |
| Comment: * |
|